KMS Service is used to activate Microsoft Windows & Microsoft Office products. It ensures that the software is legally purchased from Microsoft.
KMS is used for volume license activation.
All businesses, schools & non-profits use this KMS service.
KMS Service
You have some data and you want to protect it.
Like perhaps a credit card or a social security number.
Also, you have an encryption key and an encryption program that might do AES encryption.
Many encryption algorithms are used.
If you are doing a standard National Institute of Standards and Technology NIST type of encryption, it could be DES (Data Encryption Standard).
The encryption key is the unique bit of data that is what protects your data.
It is a secret that you have to make sure it does not get lost.
KMS service is designed to create, protect, and deliver Encryption Keys.
Either by doing Encryption or Decryption tasks.
It is deployed on a typical server that you might find in any IT computer room.
They are typically designed to be more secure.
KMS Service Components
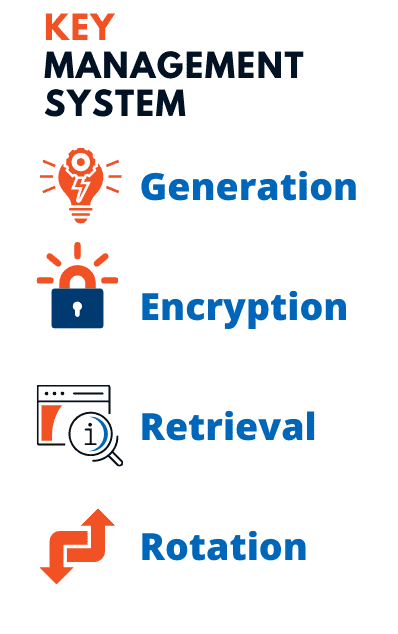
There are four main components of a KMS Service.
- Generation of Encryption Keys
- Encryption of Encryption Keys
- Retrieval of Encryption Keys
- Rotation of Encryption Keys
Encryption Key Generation
Generation is an important component.
It is relatively hard to generate a good unpredictable encryption key.
It uses a random number generator to generate them, to make sure it is unpredictable.
To do this, Cryptographically secure or True Random Number Generators are deployed.
Once it is generated then it has to be stored on a computer.
Storing it on a server is another job in itself.
This is stored in an encrypted format with some special keys called Encryption Keys.
Now that we have got the key generated and securely stored, we have to be able to retrieve them.
We should be able to bring them into our Windows mainframe or Linux applications.
So that we can use them to encrypt our data.
Encryption Key Retrieval
Key Retrieval is another important component of the KMS Service.
It is done securely.
In other words, we don’t want that key to go over the network.
So that it could not be exposed to a loss.
Retrieval is typically done with either secure SSL or TLS-type sessions.
It is wrapped in a secure package and moved over the network.
Encryption Key Rotation
Changing a key is called Key Rotation.
Many compliance regulations require that keys should be changed periodically, perhaps every 90 days or every year.
Being able to change the description or the activation and expiration dates of keys is also an important component of a system.
When you create the keys maybe you don’t want to use them for a particular period.
Likewise, if they are lost or compromised, you may want to revoke them or make them unusable.
You may even want to delete or destroy them.
These are some of the basic Functions.
They are created at the National Institute of Standards and Technology NIST.
If you want to know more about them, just Google NIST SP 800-53.
Here is a whole discussion about the Key life cycle.
This is all pretty well defined now.
What we have talked about so far in terms of creating, activating, expiring, revoking, and deleting keys.
It is all part of the key life cycle process.
It will typically give you the ability to control and access those keys.
You have to make sure that only the right people are using them.
You have to know, how many of them you have, what are their names, and what are their attributes.
So Query is another important component of the system.
This will provide a mechanism for backing up and real-time mirroring.
KMS Service Emulator
There are many tools and KMS Service emulators available.
These emulators are used to activate Windows and Office free.
Some of these tools are listed below:
Please Contact Us for your queries and suggestions.

Comments are closed.